Query Parameter Stripping
To combat Navigational Tracking through link decoration, Firefox can strip known tracking query parameters from URLs before the user navigates to them.
Protection Background
What similar protections do other browsers have?
Brave also has a list-based query parameter stripping mechanism. A list of query parameters stripped can be found here. Brave also has a strip-on-copy feature which allows users to copy a stripped version of the current URL.
Is it standardized?
At this time there are no standardized navigational tracking protections. The PrivacyCG has a work item for Navigation-based Tracking Mitigations. Also see Apple’s proposal here.
How does it fit into our vision of “Zero Privacy Leaks?”
Existing tracking protections mechanisms in Firefox, such as ETP and TCP focus mostly on third-party trackers. Redirect tracking can circumvent these mechanisms by passing identifiers through link decoration and first-party storage. Query parameter stripping contributes to the “Zero Privacy Leaks” vision by mitigating this cross-site tracking vector.
Firefox Status
Metabug: Bug 1706602 - [meta] Implement URL query string stripping prototype
What is the ship state of this protection in Firefox?
Query stripping is enabled in release in ETP strict with an initial list of query params:
mc_eid
oly_anon_id
oly_enc_id
__s
vero_id
_hsenc
mkt_tok
fbclid
It is enabled in Nightly by default in all modes with an extended strip-list. You can find the current list of parameters that are stripped here. Note that some records have a filter_expression that limits where they apply.
Is there outstanding work?
After our initial release on ETP strict, we are considering to ship the feature to Private Browsing Mode and possibly also to enable it by default in release in the future.
Other possible improvements:
Extend the list of query parameters stripped, in accordance with our policy.
Extend the protection to cover different kinds of link decoration, beyond just query parameters.
Ability to identify and strip hashed link decoration fields
Strip query params for urls shared / copied out from the browser
Outstanding bugs:
See dependencies of Bug 1706602 - [meta] Implement URL query string stripping prototype
Existing Documentation
Technical Information
Feature Prefs
| Pref | Description |
|---|---|
| privacy.query_stripping.enabled | Enable / disable the feature in normal browsing. |
| privacy.query_stripping.enabled.pbmode | Enable / disable the feature in private browsing. |
| privacy.query_stripping.allow_list | Comma separated list of sites (without scheme) which should not have their query parameters stripped. |
| privacy.query_stripping.redirect | Whether to perform stripping for redirects. |
| privacy.query_stripping.strip_list | List of space delimited query parameters to be stripped. |
How does it work?
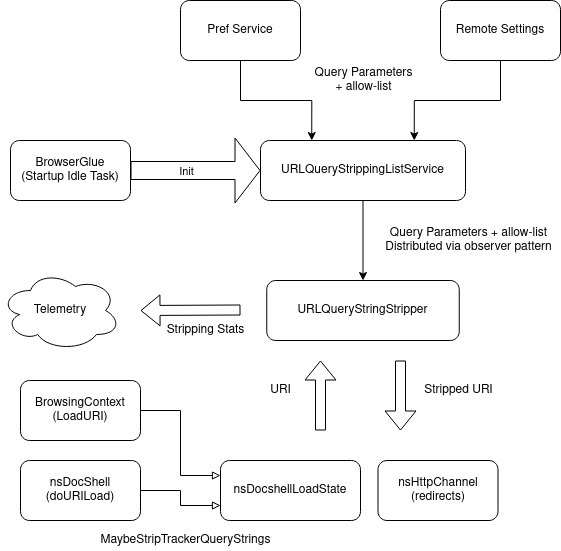
Collects list of query parameters to be stripped and allow-list from the privacy.query_stripping.strip_list/allow_list preference and the query-stripping Remote Settings collection
Lists from the two sources are concatenated
Lists are distributed via observer notification via the nsIUrlQueryStrippingListService. onQueryStrippingListUpdate is called initially on registration and whenever the preferences or the Remote Settings collection updates.
Only subscriber of the UrlQueryStrippingListService
Holds hash set representations of the strip- and allow-list.
URLQueryStringStripper::Strip: takes a nsIURI as input and strips any query parameters that are on the strip-list. If the given URI matches a site on the allow-list no query parameters are stripped.
Consumers
nsDocShell::DoURILoad: Strips in the content, before creating the channel.
BrowsingContext::LoadURI: Strips before loading the URI in the parent.
nsHttpChannel::AsyncProcessRedirection: Strips query parameters for HTTP redirects (e.g. 301).